Today is the golden age of "Internet of Things" (IoT) technology: the performance of embedded processors and the richness of on-chip resources have been greatly improved, and the functions that embedded devices can achieve are gradually diversified. Wi-Fi(wireless fidelity), Bluetooth, 5G(5th generation) and other wireless communication technologies have been fully popularized, making the threshold of the "Internet of everything" unprecedentedly lower; At the same time, the collaboration between embedded devices and smart devices such as mobile phones and routers is greatly increased, which greatly improves the functionality and user experience of embedded devices. The Internet of Things technology has penetrated into every aspect of ordinary people's lives: from sweeping robots, smart speakers and Bluetooth switches at home, to logistics robots and drones in industry, which are typical applications of the Internet of Things technology. However, the security problems of iot devices cannot be underestimated. Compared with common computing devices such as personal computers (PCS) and mobile phones in daily life, Internet of Things devices are more likely to suffer security vulnerabilities and become targets of cyber attacks. There are many reasons for this. Examples are as follows:
The computing resources of iot devices are limited, and a full operating system is usually not deployed on the device. Therefore, the binary security hardening measures commonly found on PCS and smartphones are rarely used on iot devices, such as: address space layout randomization (ASLR), disjoint writable and executable memory, stack smashing protection (SSP), etc. This makes software vulnerabilities on devices easier for attackers to exploit in order to gain control over the device.
Similarly, complex security mechanisms such as firewalls usually do not exist on Internet of Things devices, and the security of Internet of Things devices relies heavily on the security of the surrounding network environment.
The security mechanism on some (especially low-end) iot devices is too simple, and the code on the device has not been adequately audited for security, so it is more prone to security weaknesses, which increases the risk of security attacks on the device.
Internet of Things devices are more vulnerable to scanning and attacks due to their "ubiquitous", long time online nature. In particular, some devices exposed to the public network for a long time, such as routers and "Raspberry PI", are the focus of hackers to study, scan and attack. Once the iot device is attacked and enters the botnet, it is likely to cause long-term and lasting damage to other devices on the same network, and it is difficult for the device owner to find it.
The nature of iot devices makes them more sensitive to side-channel attacks at the physical level. For example, the power consumption of iot devices has a strong correlation with the execution state of cpus. It is easy for attackers to calculate the execution state of cpus indirectly by measuring the power changes of iot devices, and leak confidential information such as user passwords. In addition, iot devices are also more sensitive to denial of service (DoS) attacks. For example, attackers can realize the purpose of wasting the life of an iot device by repeatedly waking it up.
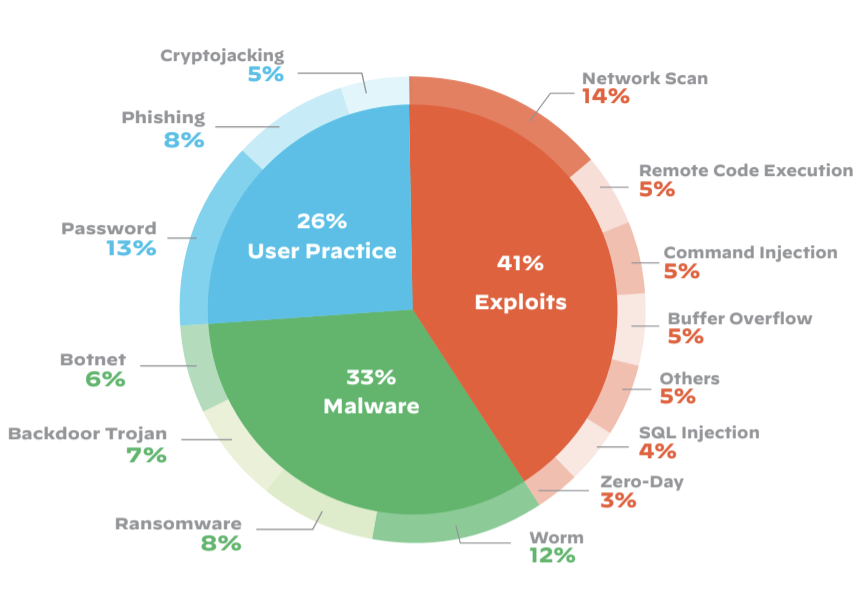
Figure 1 Types of attacks against iot devices
Because of the above reasons, security analysis and hardening for iot devices are very different from traditional PC devices, and the field of iot security needs guidance of new technologies and methods. At present, the academia and the industry have some research on the security of the Internet of things, but the industry for the Internet of Things equipment security degree is generally insufficient, network attacks against the Internet of Things equipment is still very active. Due to the steady increase in the market share of iot devices, iot security has gradually become an important topic in the field of information security.
It mainly consists of 4 parts. In the first part, we briefly explain the current state of iot technology and the reasons why iot devices are vulnerable to security threats. In Part 2, we will review the major threats facing existing iot devices. In Part 3, we will describe some of the security mechanisms that are unique to iot devices. In Part 4, we will briefly describe some of the security practices currently established in the industry for iot devices. Finally, we will summarize the whole paper.
2. Security threats against Internet of Things devices
Traditionally, an iot system can be roughly divided into 3 levels, which are:
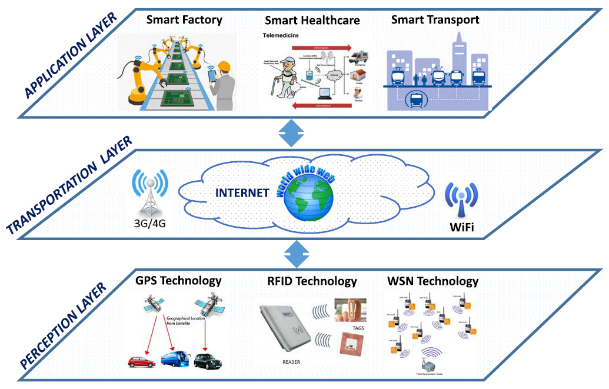
Figure 2 Internet of Things system model
1. perception layer:responsible for providing physical sensors and communication networks, such as RFID, radio frequency identification, GPS, global positioning system, etc.;
2. transportation layer:responsible for establishing communication between Internet of Things devices and the Internet, such as Bluetooth gateway;
3. application layer:responsible for realizing the functions of Internet of Things devices, such as automatic pathfinding of sweeper robots and voice recognition function of smart speakers. The characteristics of these three different layers are different, so they also face different security threats, as detailed below.
Perception layer security. The main threats to the perception layer are of the following types:
Physical attacks. After gaining physical access to a device, an attacker will be able to extract sensitive data directly from the device or modify programs on the device to insert malicious code into it. Such attacks require physical contact with a device, making them relatively easy to guard against; However, it is also necessary for device manufacturers to consider the physical security of the device itself, for example, to avoid leaving debugging interfaces on the circuit board of the device.
Identity camouflage. In iot networks that lack effective authentication measures, the problem of identity impersonation is prone to occur, and malicious devices can steal sensitive data in this way. In addition, insecure device initialization and pairing processes are also important sources of security threats, such as an attacker who can take advantage of a router being turned on for the first time, without a password, to inject malicious programs or configurations into it. To prevent such attacks, device manufacturers should carefully consider possible security issues during authentication and include effective authentication mechanisms.
Denial of service attack (DoS). An attacker can deplete a device's computing power by keeping it in a high power state for a long period of time. It is very difficult to prevent such attacks completely, but device manufacturers can minimize the damage caused by such attacks through reasonable security design. For example, for operations that require a lot of computing power, effective client-side authentication mechanisms should be incorporated, or the frequency of operations performed by the client should be limited, etc.
Data transfer attacks. For example, an attacker can capture the data transmitted by a device, or carry out a MitM (man in the middle) attack. The common defense against such attacks is to add encryption and security verification mechanisms during data transmission, such as Wi-Fi Protected Access (WPA) in Wi-Fi. And EEA(EPS Encryption Algorithm) in Long Term Evolution; EPS = Evolved Packet System) algorithm and so on.
Transport layer security. The security threats at this layer mainly involve the security threats to the access network (such as Wi-Fi and 5G). There are two types of attacks, namely, data transmission attack and denial of service attack. The defense methods of these two types of attacks are similar to those of the perceptual layer security, which will not be discussed here. Application layer security. Security threats at this layer coincide with those faced by traditional PCS to some extent, mainly including the following types:
Data leakage: Design omissions in the program may lead to the disclosure of users' private data to the third party. To minimize such vulnerabilities, an adequate security audit and evaluation of the program code on the device is required.
Denial of service attacks: Similar to denial of service attacks in awareness layer security, we will not go into details here.
Remote code execution: Using the security holes in the device program, the attacker can control the device to perform some unexpected actions, or even execute any code uploaded by the attacker. The prevention methods of such security threats are similar to those of traditional vulnerabilities, including: strengthening code security audit, fuzzing the program, and adopting binary security hardening measures such as ASLR. However, when guarding against such vulnerabilities, the resource limitations of the device should be considered at the same time.

